The ACSC Essential 8
What is the essential 8 and why do I need it?
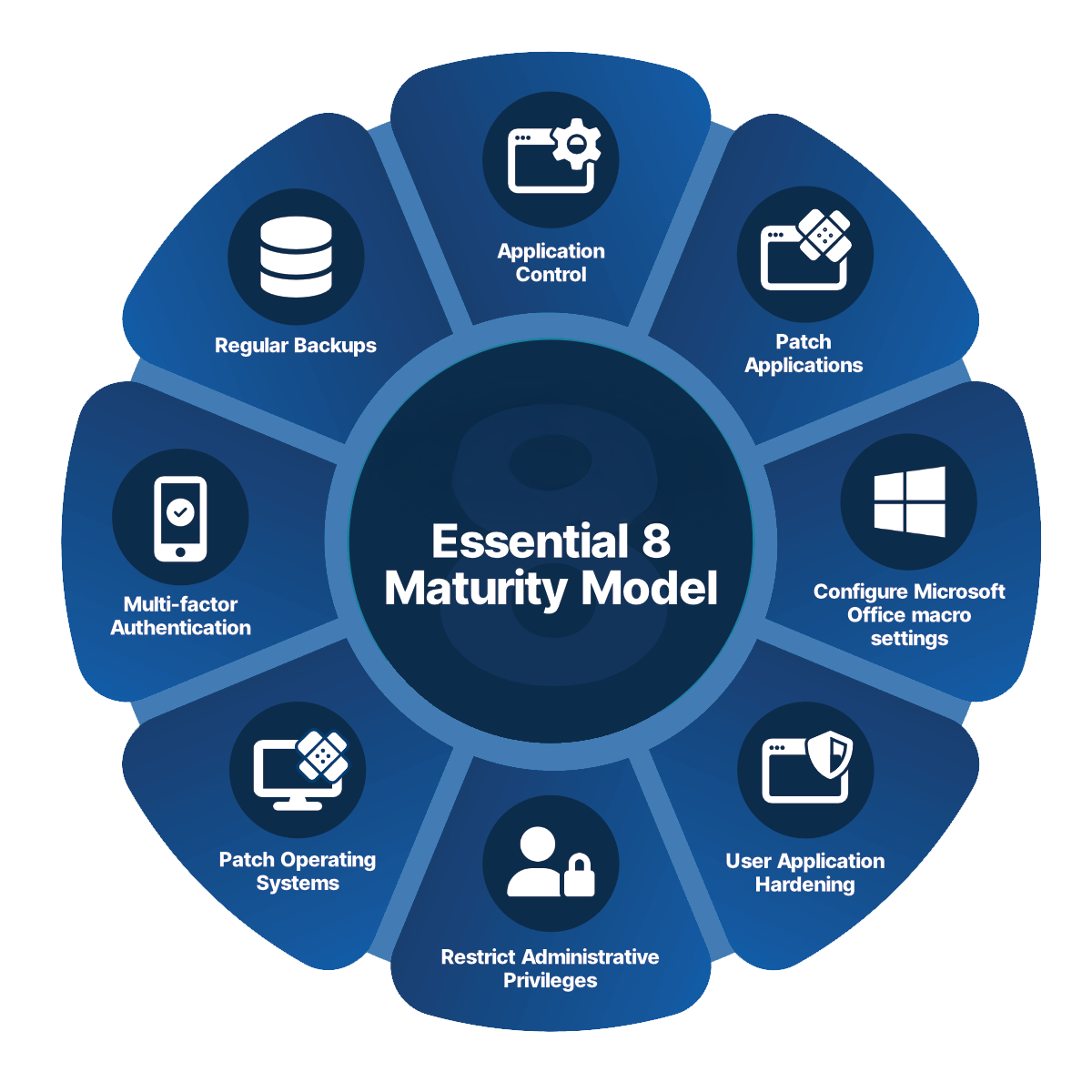

Essential 8 Maturity Levels – Simplified Overview
Maturity Level 1 – Targets opportunistic attackers who use widely available exploits and stolen credentials to gain access. They rely on common social engineering and weak security measures, often compromising unpatched systems or weak passwords. If they gain privileged access, they may destroy data, including backups.
Maturity Level 2 – Threat actors invest more time and effort in targeting victims, using phishing and social engineering to bypass security controls, including weak multi-factor authentication. They are more selective in choosing victims and focus on stealing credentials or escalating privileges.
Maturity Level 3 – Highly adaptive attackers use customized techniques to exploit security weaknesses, evade detection, and maintain access. They employ advanced social engineering, token theft, and privilege escalation to move laterally within networks. These actors are more persistent and may erase all data and backups to maximize damage.
